Detecting And Combating Malicious Email
It is increasingly necessary for all email users to understand how to recognize and combat malicious email. Read a review of it here by Help Net Security contributor Zeljka Zorz.
 Malicious Email An Overview Sciencedirect Topics
Malicious Email An Overview Sciencedirect Topics
Julie Ryan is currently an Associate Professor and.

Detecting and combating malicious email. Jan 06 2015 Download PDF 73KB Safe emailing everyone. If you feel like you need to examine an attachment you can save it to a. How are ratings calculated.
Jan 05 2015 Detecting and Combating Malicious Email. Oxford Elsevier LTD Nov 2014 2014. Detecting and Combating Malicious Email describes the different types of malicious email shows how to differentiate malicious email from benign email and suggest protective strategies for both personal and enterprise email environments.
Mar 18 2016 The following is an excerpt from the book Detecting and Combating Malicious Email written by authors Julie JCH Ryan and Cade Kamachi and published by Syngress. Complement email security with user awareness and training. In this section from chapter four learn about three main elements.
Up to 5 cash back Detecting and Combating Malicious Email describes the different types of malicious email shows how to differentiate malicious email from benign email and suggest protective strategies for both personal and enterprise email environments. To download Detecting and Combating Malicious Email PDF make sure you refer to the link listed below and download the file or have accessibility to other information that are relevant to DETECTING AND COMBATING MALICIOUS EMAIL ebook. It is increasingly necessary for all email users to understand how to recognize and combat malicious email.
First use the technology to help you as much as it can and second use your brain. Detecting and Combating Malicious Email describes the different types of malicious email shows how to differentiate malicious email from benign email and suggest protective strategies for both personal and enterprise email environments. Scientists and researchers are continually applying every trick possible to combat malicious email and significant advances have been made.
It is among the most incredible publication i have go through. Detecting and Combating Malicious Email describes the different types of malicious email shows how to differentiate malicious email from benign email and suggest protective strategies for both personal and enterprise email environments. Add to Wish List.
Detecting and Combating Malicious Email describes the different types of malicious email shows how to differentiate malicious email from benign email and suggest protective strategies for both personal and enterprise email environments. Detecting and Combating Malicious Email describes the different types of malicious email shows how to differentiate malicious email from benign email and suggest protective strategies for both personal and enterprise email environments. Implement multi-factor authentication to prevent account takeover and disable legacy authentication.
Eventually all of us will open a malicious email and fall for a. Scientists and researchers are continually applying every trick possible to combat malicious email and significant advances have been made. Julie JCH Ryan and Cade Kamachi Pages.
It is increasingly necessary for all email users to understand how to recognize and combat malicious email. Detecting and Combating Malicious Email describes the different types of malicious email shows how to differentiate malicious email from benign email and suggest protective strategies for both personal and enterprise email environments. Neuware - Primer on Flat.
First use the technology to help you as much as it can and second use your brain. Detecting and Combating Malicious Email. 1 day agoUpgrade to an email security solution that provides advanced phishing protection business email compromise detection internal email protection and account compromise detection.
Again the first order recommendation is never to launch an attachment from within an electronic message. Jun 18 2013 There are two major components to detecting and combatting malicious email. There are two major components to detecting and combatting malicious email.
Selecting copy and then mov- ing to a note taking application where the link was pasted reveal its entire structure. It is increasingly necessary for all email users to understand how to recognize and combat malicious email. Learn more from Julies book Detecting and Combating Malicious Email and Save Up to 40 on Syngress.
Cybersecurity Resources on Amazon through August 15 th. 2 global ratings 1 global review There was a problem filtering reviews right now. By Julie JCH Ryan.
DETECTING AND COMBATING MALICIOUS EMAIL - To save Detecting and Combating Malicious Email PDF remember to access the hyperlink beneath and save the document or have access to additional information which are highly relevant to Detecting and Combating Malicious Email book. You can see the actual link in light gray at the top of this menu. 54 Detecting and Combating Malicious Email In this example the copying process was started by pressing and holding the link until the copy menu came up.
PDF Detecting and Combating Malicious Email Detecting and Combating Malicious Email Book Review These kinds of ebook is the perfect publication offered. You will not feel monotony at whenever you want of your time thats what catalogues are for concerning if you check with me. It is increasingly necessary for all email users to understand how to recognize and combat malicious email.
16 Detecting and Combating Malicious Email attachment in the electronic message launches the file via the default application for that file type. See All Buying Options.
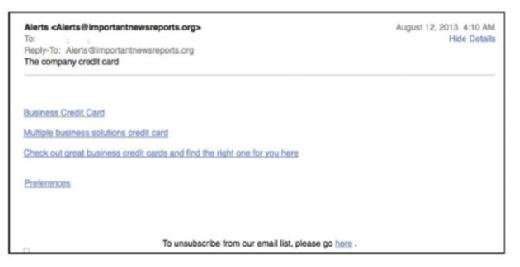 Detecting And Combating Malicious Email
Detecting And Combating Malicious Email
 Malicious Email An Overview Sciencedirect Topics
Malicious Email An Overview Sciencedirect Topics